Today we will cover how to disable weak cbc ciphers in ssh server, after this you will pass cbc ciphers vulnerability.
Red Hat Enterprise Linux 8.x
OpenSSH
Tool used for vulnerability checking
There were 2 server affected in total so i will try to do explain in three parts, First part consist adding policy (optional), Second is enabling specific policy instead of default site-wide policy, Third part has 2 methods for me both has worked, you can choose one of them.
First open terminal and type
update-crypto-policies --show
by default you will get reply as
DEFAULT
then please change it to FUTURE, for that type
reboot server, most probably this wont work, for me also it didn’t work, i included this because in every tutorial it is mentioned. now go to step 2.
to enable specific CRYPTO_POLICY instead of using system-wide policy, you need to uncomment the line ” CRYPTO_POLICY” from /etc/sysconfig/sshd
Open /etc/sysconfig/sshd and uncomment from .
Now we need to set SSHD specific policy for CBC ciphers, you can do this by modifying line found in /etc/ssh/sshd_config.
after adding method 1 to /etc/ssh/sshd_config , during restarting ssh server you may face issue, just commend before public key, and it worked for me, to find why ssh server failed to start you can use following command.
edit /etc/ssh/sshd_config and add following lines, in Method 1 you may face issue when trying to restart ssh server, type
[email protected],
[email protected],aes256-ctr,
[email protected],aes128-ctr
GSSAPIKexAlgorithms=gss-gex-sha1-,gss-group14-sha1-
[email protected],ecdh-sha2-nistp256,ecdh-sha2-nistp384,ecdh-sha2-nistp521,diffie-hellman-group-exchange-sha256,diffie-hellman-group14-sha256,diffie-hellman-group16-sha512,diffie-hellman-group18-sha512,diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1
HostKeyAlgorithms=rsa-sha2-256,
[email protected],ecdsa-sha2-nistp384,
[email protected],rsa-sha2-512,ecdsa-sha2-nistp521,
[email protected],ssh-ed25519,
[email protected],ssh-rsa,
[email protected]
PubkeyAcceptedKeyTypes=rsa-sha2-256,ecdsa-sha2-nistp256,
[email protected],ecdsa-sha2-nistp384,
[email protected],rsa-sha2-512,ecdsa-sha2-nistp521,
[email protected],ssh-ed25519,
[email protected],ssh-rsa,
[email protected]
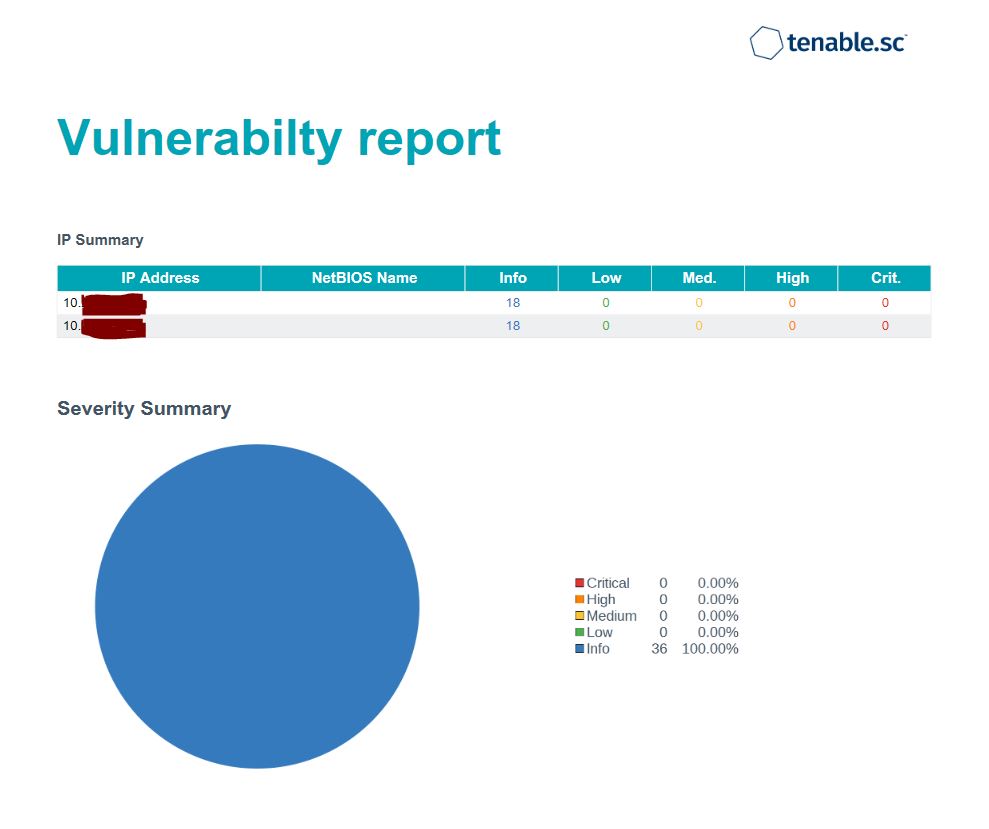
Now you can do vulnerability test again, it must be fix by now, Enjoy






0 Comments