NIMIQ Will cryptocurrency replace traditional money? The question is not if but when. So what does it takes to empower real mass adoption? Bitcoin set...
OS
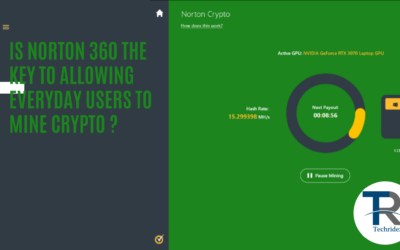
Is Norton 360 the key to Allowing Everyday Users to mine Crypto ?
By 2030, studies show that blockchain technology is expected to lift the global GDP up by two trillion US dollars. As more countries are setting trends in...
Chia Cryptocurrency
Chia is a cryptocurrency using a block chain technology.and it uses what is called a proof of space and work consensus mechanism. In short to farm anything...
How to reset forgotten root password in FreeBSD.
FreeBSD is an operating system used to power modern servers, desktops, and embedded platforms. A large community has continually developed it for more than...
How to Reset forgotten the Root Password in ubuntu server
If you forget your root password of your ubuntu server you can use this method.If you are using a bare metal server or a vps all you have to do is restart...
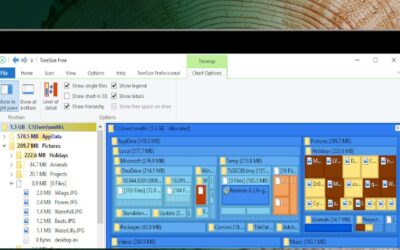
Best application to find where space is being taken up on your Windows PC or Server.
When ever you got alert on your PC that Hard drive didn't have much space left, first thing we all do is clearing temp, uninstalling unwanted application or...

Subscribe For Instant News, Updates, and Discounts
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Curabitur arcu erat, accumsan id imperdiet et, porttitor at sem.